
Not to be confused with an aquatic hunt on a tropical vacation, spear phishing is a cyberattack that targets a specific individual or organization in order to get confidential information for fraudulent purposes. Learn how spear phishing works and how to protect yourself. Then, get comprehensive online security to help protect against spear phishing attacks, malware, and other online scams.


Spear phishing is a type of phishing attack in which a cybercriminal targets a specific individual or entity through text messages or emails in order to gain access to sensitive information. To gain the trust of victims, spear phishing campaigns often include information that the victim is interested in.
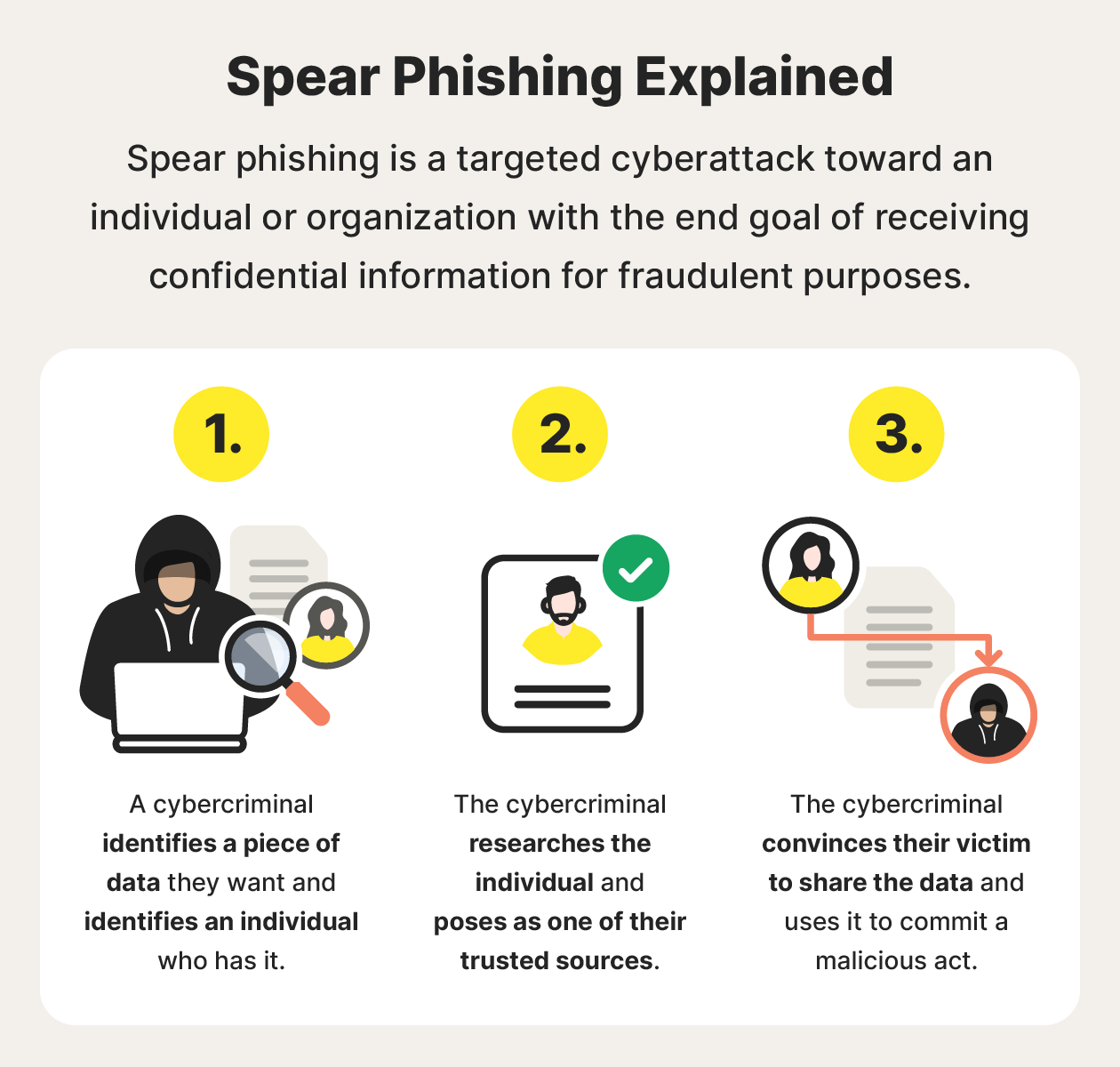
To prepare for a spear phishing attack, a cybercriminal researches their victims to gather information they can use to pass as a trustworthy source. Using that info, the spear phisher contacts their victim through text message or email, trying to get them to click a malicious link or divulge confidential data or other sensitive details.
The cybercriminal then uses this information for malicious purposes, which may include identity theft or data breaches.
Here's the detailed process of how a spear phishing attack works:
The success of a spear phishing campaign largely depends on how much research and customization goes into the attack. Hacktivists and government-sponsored hackers are often identified as being behind spear phishing attacks, because they focus on quality over quantity.
To appear as trustworthy sources, spear phishers do a great deal of reconnaissance on their victims, which is one of the biggest differences between traditional phishing and spear phishing. Because of the detail and personalization that often goes into an attack, spear phishing can be understood as a form of social engineering.
The biggest difference between traditional phishing and spear phishing is that a spear phishing attack targets a specific person or organization, while phishing is a more generic cyberattack aimed at a large group.
Spear phishers carefully research potential victims to find those that have the data or information they want, and they customize their messages to convince their victims to trust them.
Phishing emails are often sent to hundreds or thousands of recipients simultaneously with little customization in messaging. Spear phishers, however, often pose as a friend, boss, family member, or well-known brand to gain your trust and fool you into giving them information.
Ultimately, the intent of phishing and spear phishing is the same — acquiring private information for malicious purposes. But because spear phishing attacks are well-researched with more customized, personalized messaging, they can be very hard to detect.

Spear phishing techniques differ, depending on the type of information the spear phisher wants and who they’re targeting. Here are a few spear phishing examples to consider:
Not to be confused with whaling — a phishing attempt targeting a C-suite executive — CEO fraud scams are a type of spear phishing scam in which cybercriminals pose as a C-suite executive to get an employee to fulfill an urgent request or divulge important data.
For example, a “CEO” might email an employee on a weekend and ask them to complete a wire transfer to a contractor. But if the employee completes the transfer, they could simply be transferring company funds to the spear phisher’s account.
Spear phishing emails don’t always ask for sensitive data directly. Instead, they might send you malware via email attachments.
For example, a spear phisher might pose as a service provider and send you an attached invoice. Then, if you click that attachment, malware or a keylogger that traces your activity could be downloaded onto your device.